Advanced Threat Analytics Security Operations add-on for Splunk
Splunk integration setup
Setup procedures for the Security Operations add-on for Splunk include downloading the add-on file in Splunk, installing the add-on, and setting up the Advanced Threat Analytics instance where security incidents and events are created.
Required Information
Before performing Splunk integration setup procedures, ensure that you have the integration information for your specific user:
- Unique organization ID
- Authorization token
The first step in setting up the Advanced Threat Analytics-to-Splunk integration is to download the Advanced Threat Analytics Security Operations application from Splunkbase.
Install and Configure the Advanced Threat Analytics Security Operations add-on for Splunk
Install the Advanced Threat Analytics Security Operations add-on for Splunk to link Splunk to Advanced Threat Analytics.
- Open Splunk
- Click either the Apps gear icon, or the Manage Apps shortcut menu item.
- Click Install app from file.
- Click Choose File, select ataportal_app.spl, and click Upload.
- Click the "Set up now" button to configure the app for your organization. You MUST be a customer of ATA or MSSP that leverages the ATA Platform.
- Provide the Advanced Threat Analytics Server URL, Authorization Token, and your Customer ID (unique Organization ID).
The Advanced Threat Analytics Security Operations add-on for Splunk is installed and ready to be set up.
Configure the App for your Organization
Single-record Splunk alerts
Within any alert, you can specify security events to be sent to the ATA Platform when the alert is fired.
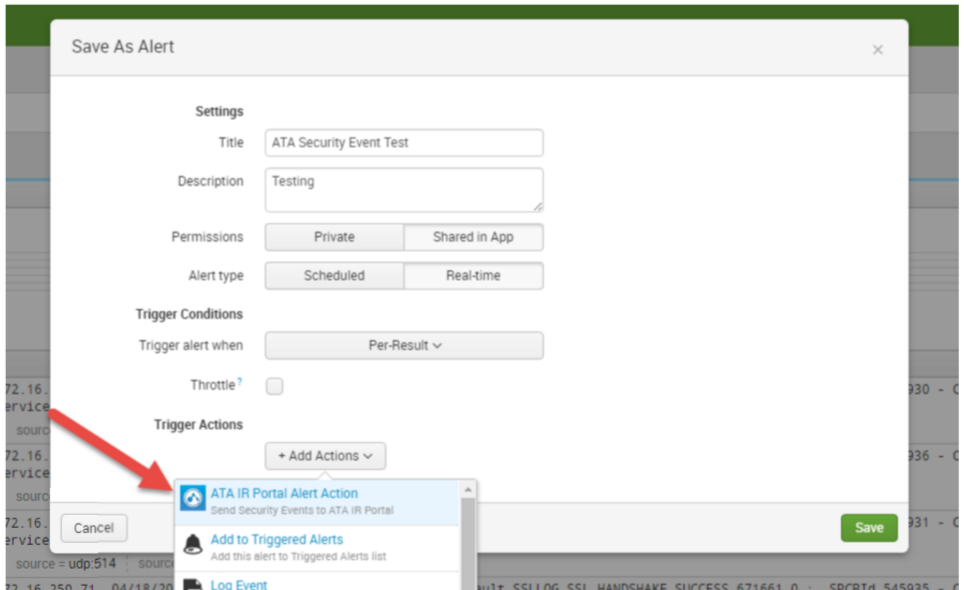
Open or create your alert, and when editing actions, select the "ATA IR Portal Alert Action", and fill in the alert dialog box.
To create an alert from a Search, simply "Save As" an Alert.
If you are uncertain about the Alert settings, use the following options
- Permissions: Shared in App
- Alert Type: Real-time
- Trigger Alert: Per-result
After adding the Action, you will be able to add additional fields that can be customized on a per Alert basis. These fields are optional and include the following. Any of these fields that are sent, with the exception of “Title” and “Event Grouping” can be used for searching and filtering on the ATA IR Portal. :
- Title, override the default Incident Title that’s created by ATA IR Portal
- Event Grouping – how the ATA Portal will group events. This should be one of the fields present in the log event. Leave blank to use ATA Portal default (hostname or IP address).
- Category – category of the Security Event sent
- Priority – Priority of the Security Event sent
- Type – Type of the Security Event being sent
Save Alert.
Alert Should show up in the list of Alerts.
Alert View.